
A macOS model of the LightSpy surveillance framework has been found, confirming the in depth attain of a instrument solely beforehand recognized for focusing on Android and iOS units.
LightSpy is a modular iOS and Android surveillance framework used to steal all kinds of knowledge from folks’s cell units, together with information, screenshots, location knowledge (together with constructing flooring numbers), voice recordings throughout WeChat calls, and fee info from WeChat Pay, and knowledge exfiltration from Telegram and QQ Messenger.
The attackers behind the framework use it in assaults in opposition to targets within the Asia–Pacific area.
Based on a brand new report by ThreatFabric, a macOS implant has been found to be lively within the wild since no less than January 2024. Nonetheless, its operation seems to be presently restricted to testing environments, and a handful of contaminated machines are utilized by cybersecurity researchers.
The researchers infiltrated LightSpy’s management panel by exploiting a misconfiguration that allowed unauthorized entry to the authenticated interface, gaining insights into the performance, infrastructure, and contaminated units.
Utilizing exploits to compromise macOS
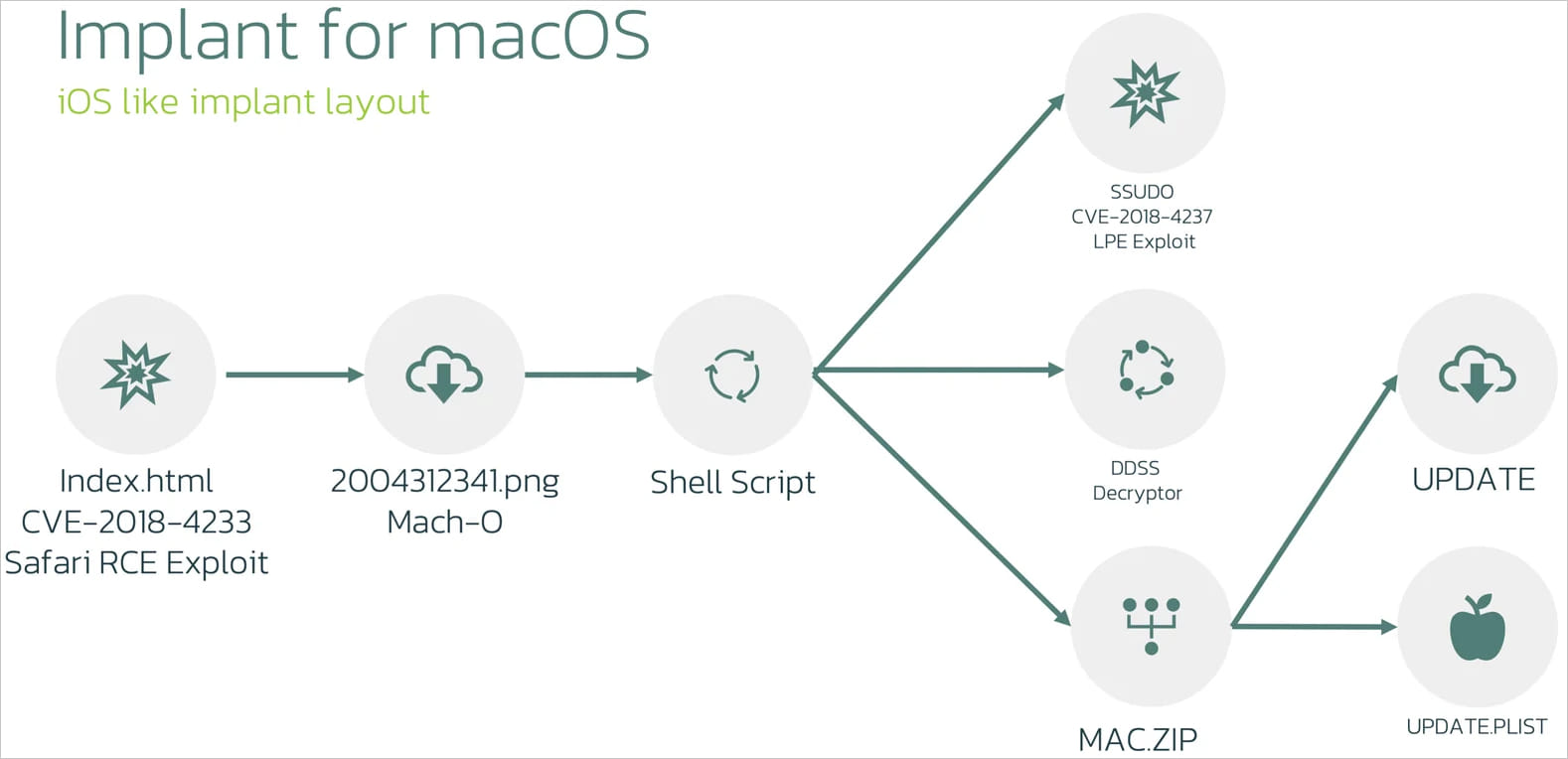
The risk actors use WebKit flaws CVE-2018-4233 and CVE-2018-4404 to set off code execution inside Safari, focusing on macOS 10.13.3 and earlier.
Supply: ThreatFabric
Initially, a 64-bit MachO binary disguised as a PNG picture file (“20004312341.png”) is delivered on the machine, decrypting and executing embedded scripts that fetch the second stage.
The second stage payload downloads a privilege escalation exploit (“ssudo”), an encryption/decryption utility (“ddss”), and a ZIP archive (“mac.zip”) containing two executables (“replace” and “replace.plist”).
Ultimately, the shell script decrypts and unpacks these information, gaining root entry on the breached machine and establishing persistence on the system by configuring the “replace” binary to run at startup.
Supply: ThreatFabric
The subsequent step is carried out by a part referred to as “macircloader,” which downloads, decrypts, and executes LightSpy Core.
This acts because the central plugin administration system for the adware framework and is chargeable for communications with the command and management (C2) server.
LightSpy core also can execute shell instructions on the machine, replace its community configuration, and set an exercise timetable to evade detection.
LightSpy plugins
The LightSpy framework extends its spying performance utilizing varied plugins that carry out particular actions on the compromised machine.
Although the malware makes use of 14 plugins on Android and 16 plugins on its iOS implant, the macOS model makes use of the next ten:
- soundrecord: Captures sound from the microphone.
- browser: Extracts shopping knowledge from in style internet browsers.
- cameramodule: Takes images utilizing the machine’s digicam.
- FileManage: Manages and exfiltrates information, particularly from messaging apps.
- keychain: Retrieves delicate info saved within the macOS Keychain.
- LanDevices: Identifies and gathers details about units on the identical native community.
- softlist: Lists put in functions and working processes.
- ScreenRecorder: Data the machine’s display exercise.
- ShellCommand: Executes shell instructions on the contaminated machine.
- wifi: Collects knowledge on Wi-Fi networks the machine is related to.
These plugins allow LightSpy to carry out complete knowledge exfiltration from contaminated macOS programs, whereas its modular design offers it operational flexibility.
ThreatFabric notes in its report that their entry to the attacker’s panel confirmed that implants for Home windows, Linux, and routers exist however couldn’t decide how they’re utilized in assaults.
“Regardless of our findings, some facets of the LightSpy puzzle stay elusive,” concludes ThreatFabric.
“There is no such thing as a proof confirming the existence of implants for Linux and routers, neither is there info on how they could be delivered. Nonetheless, their potential performance is understood based mostly on panel evaluation.”


